ARE YOU STRESSING OVER YOUR NETWORK GOING OFFLINE DUE TO A DDOS ATTACK? DON'T WORRY WE HAVE YOU PROTECTED!
What Are DDoS mitigation?
The term ‘DDoS mitigation’ refers to the process of successfully protecting a target from a distributed denial of service (DDoS) attack. A typical mitigation process can be broadly defined by these four stages:
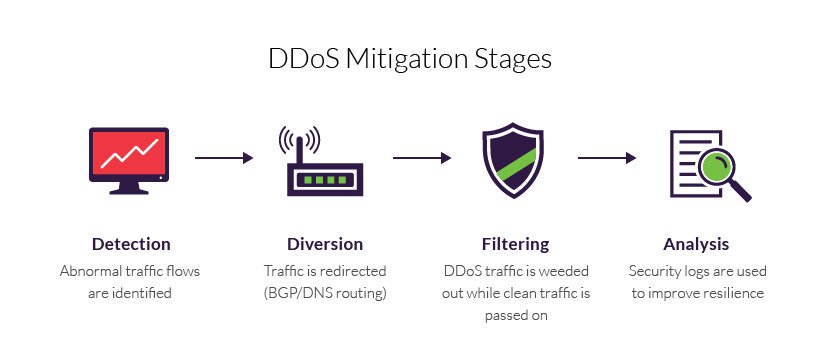
First, let's talk about the different stages of DDoS mitigation into detail.
Detection - The identification of traffic flow deviations that may signal the buildup of a DDoS assault. Effectiveness is measured by your ability to recognize an attack as early as possible, with instantaneous detection being the ultimate goal.
Diversion - Traffic is rerouted away from its target, either to be filtered or completely discarded.
Filtering - DDoS traffic is weeded out, usually by identifying patterns that instantly distinguish between legitimate traffic (i.e., humans, API calls and search engine bots) and malicious visitors. Responsiveness is a function of your being able to block an attack without interfering with your users’ experience. The aim is for your solution to be completely transparent to site visitors.
Analysis - Security logs are reviewed to gather information about the attack, both to identify the offender(s) and to improve future resilience. The process’s effectiveness relies on the existence of detailed security logs that can offer granular visibility into the attack traffic.
Why should you choose LayerHost as your provider?
Besides the method of traffic diversion, there are several other key aspects you must consider when choosing LayerHost as a provider. These include:
1. Our 4Tbps DDoS Absorbtion Capacity
Our 4Tbps DDoS network capacity remains a great way of bench-marking our DDoS mitigation service. It’s measured in Tbps (terabits per second) not Gbps (gigabits per second) and it reflects greatly to our overall scalability available to you, during an attack. For example, a 4 Tbps network can theoretically block up to the same volume of attack traffic, minus the bandwidth required to maintain its regular operations. With such a high capacity like ours there is absolute no worries about getting null-routed due to reaching your DDoS mitigation capacity.
2. Time to mitigation
Once an attack has been detected, time to mitigation is critical. Most assaults can take down a target in a matter of minutes and the recovery process can take hours. The negative impact of such downtime can potentially be felt by your organization for weeks and months ahead. By LayerHost providing a preemptive detection, our always-on solutions have a distinct advantage here. We offer near-instant mitigation—often protecting organizations from the first salvo during any assault. But not all always-on solutions offer such a response level. That is why it's always best for you to request a free month trial so we can see what attacks you usually get and how we can help to adjust to make the mitigation process as easy as possible.
3. Pricing and SLA
Pricing for DDoS mitigation services range from flat monthly fees to one-time-token offers. More information can be discussed by contacting us today!
The latter is based on cumulative attack bandwidth or cumulative number of hours under attack. Since a DDoS assault can last several hours or days (and sometimes weeks), such costs can quickly get out of hand. This is why LayerHost offers a flat monthly fee is generally preferable for long-term agreements.
Our service level agreement (SLA) is another important consideration—sometimes more so than the price. Here, to be insured we have the following:
Uptime guarantee – Five nines (99.999%) represents the best case. Anything below three nines (99.9%) is unacceptable.
Protection levels – As described herein, LayerHost’s SLA should define attack types, size and duration that it covers.
How does LayerHost implement their 4Tbps DDoS Mitigation Service?
As a stand-alone service.
In order to use our stand-alone service you will need to qualify for either of the solutions below
Anti-DDoS Tunnel for Networks
Good For:
Any customer who owns their AS number (ASN) located anywhere around the world.
What this means is:
We will establish a BGP connection inside a GRE or L2TP tunnel over the public internet. Traffic flows unfiltered unless an attack is automatically detected. If a DDoS attack is detected the bad traffic would then flow through our scrubbing centers and the clean network would be returned back to your infrastructure. In order for this to be possible network connection should established through a tunnel from each edge router it has.
Direct Physical Uplink Connection
Good For:
Any customer who owns their AS number (ASN) and a physical PoP location in a large data center near our scrubbing center.
What this means is:
We will establish a BGP connection over a fiber uplink that has in-line DDoS filters. Traffic flows unfiltered unless an attack is automatically detected. If a DDoS attack is detected the bad traffic would then flow through our scrubbing centers and the clean network would be returned back to your infrastructure. In order for this to be possible the customer must have a physical presences near our scrubbing data center.
The LayerHost Advantage
Why Our Service(s) Sets Us Apart

Why You Should Choose Us
- True 24/7/365 on-site remote hands service
- State-of-the-art data centers
- Scalability Plus package for our clients and their growing businesses
- Highly-secure facilities including: 24/7/365 patrolling guards, bio-metric access points, bulletproof windows and active CCTV monitoring
- High uptime and reliability
- Easy access to facilities with access pass
- Our expert customer service
Frequently asked questions and answers
Still have questions about our DDoS mitigation service?
- 1. Will I ever get null-routed or black-holed?
With a DDoS mitigation capacity of 4Tbps we have not nulled one customer for using our service. Simply, no we do not null route your IP if we can't handle it.
- 2. Do you charge a set-up fee on our DDoS mitigation service?
- 3. Is LayerHost's DDoS mitigation perfect?
- 4. Once ready do I need to commit to a long term?
- 5. Where are your data centers located?
- 6. Will I get access to DDoS reports?
- 7. Will I stop worring about network outages with LayerHost's mitigation service?